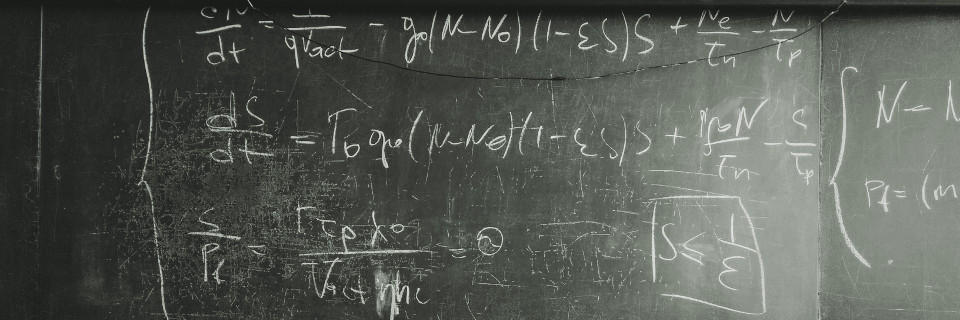About us

SEKTOR7 is a small information security research company based in Poland, EU, focusing on developing new and refined offensive techniques and technologies.
SEKTOR7 was founded in 2017. Our team has a vast experience backed by many years of research and work for external companies from the following, but not limited to, industries:
- Finance
- Technology
- Energy
- Software
- Aviation
- Transportation
Apart from pure offensive research, we deliver various information security training in the following domains:
- offensive security tools (OST) development
- threat simulations
- offensive counterintelligence
- network security
- software exploitation
- malware analysis
- web security
- hardware exploitation
SEKTOR7 supports x33fcon conference, an annual gathering of Blue and Red Teams in Europe.
Research Lab
 "Failure is the key to success; Each mistake teaches us something."
"Failure is the key to success; Each mistake teaches us something."
Morihei Ueshiba, The Art of Peace
SEKTOR7 Research Lab focuses on developing novel and evolving existing offensive techniques in information security world. These include attacks on:
- *NIX-based OS
- Windows OS
- applications
- networks
- communication technologies
We also develop new offensive tactics for long-term cyberoperations and threat simulations. Some of our work is being published at security conferences and blog posts.
If you want to become our client and learn more about our research and capabilities, please contact us directly: research (at) sektor7.net .
Training
 "Progress comes to those who train and train; reliance on secret techniques will get you nowhere."
"Progress comes to those who train and train; reliance on secret techniques will get you nowhere."
Morihei Ueshiba, The Art of Peace
Currently we offer online courses helping in building up a solid red team operator skillset, necessary in conducting the effective threat simulations. Online courses can be found in our Institute:
- RED TEAM Operator: Malware Development Essentials course - This course will teach you how to become a better ethical hacker, pentester and red teamer by learning offensive security tools (OST) development. It covers developing droppers, trojans and payload/DLL injectors using some basic C and Intel assembly skills.
- RED TEAM Operator: Malware Development Intermediate course - More advanced offensive security tools (OST) development techniques in Windows, including: API hooking, 32-/64-bit migrations, reflective binaries and more.
- RED TEAM Operator: Malware Development Advanced (vol.1) course - Advanced offensive security tools (OST) development topics for Windows user land only, including: hidden data storage, rootkit techniques, finding privileged objects in system memory, detecting new process creation, generating and handling exceptions, building COFFs and custom RPC-like instrumentation, and more.
- RED TEAM Operator: Malware Development Advanced (vol.2) course - Advanced offensive security tool (OST) development for Windows kernel, including: kernel object manipulations, silencing EtW telemetry, obtaining and preserving READ+WRITE primitives in Windows kernel, and more.
- RED TEAM Operator: Windows Evasion course - Learn how to avoid modern endpoint protection technology with well known, less known and in-house developed techniques
- RED TEAM Operator: Privilege Escalation in Windows course - A course about breaking and bypassing Windows security model. Escalating privileges with 20 different techniques. From non-admin to SYSTEM.
- RED TEAM Operator: Windows Persistence course - 27 persistence methods in Windows. From basic to advanced, unique and known, used in malware like Stuxnet or Flame and by nation-state threat actors, including EquationGroup, Turla and APT29.
Contact

Please feel free to contact us: enquiries@sektor7.net